Embarking on a Docker Networking Project as Part of the Learning Journey
Types of Docker networking
In the dynamic world of containerization, Docker has emerged as a key player, revolutionizing the way one deploys and manages applications. But what about the intricate web that connects these containers? Docker networking, often thought of as something complex plays a pivotal role in ensuring seamless communication between containers. Join me as I dive deep into the realm of Docker networking. Talk about what is Docker networking, and its type and also create a default network for Two Tier applications using Docker.
Types of Docker Networks
When we talk about docker networks we get to see three types of networks that come in default with docker.
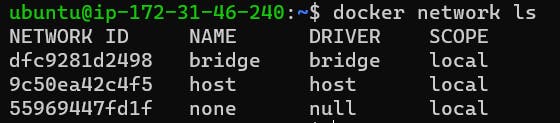
Let's discuss first each of them in detail.
Default Bridge
In Docker, a "bridge" is a default networking mode that allows containers to communicate with each other and with the host system over a virtual network. The default bridge network is created automatically when you install Docker on your system, and containers are attached to this network by default unless you specify a different network.
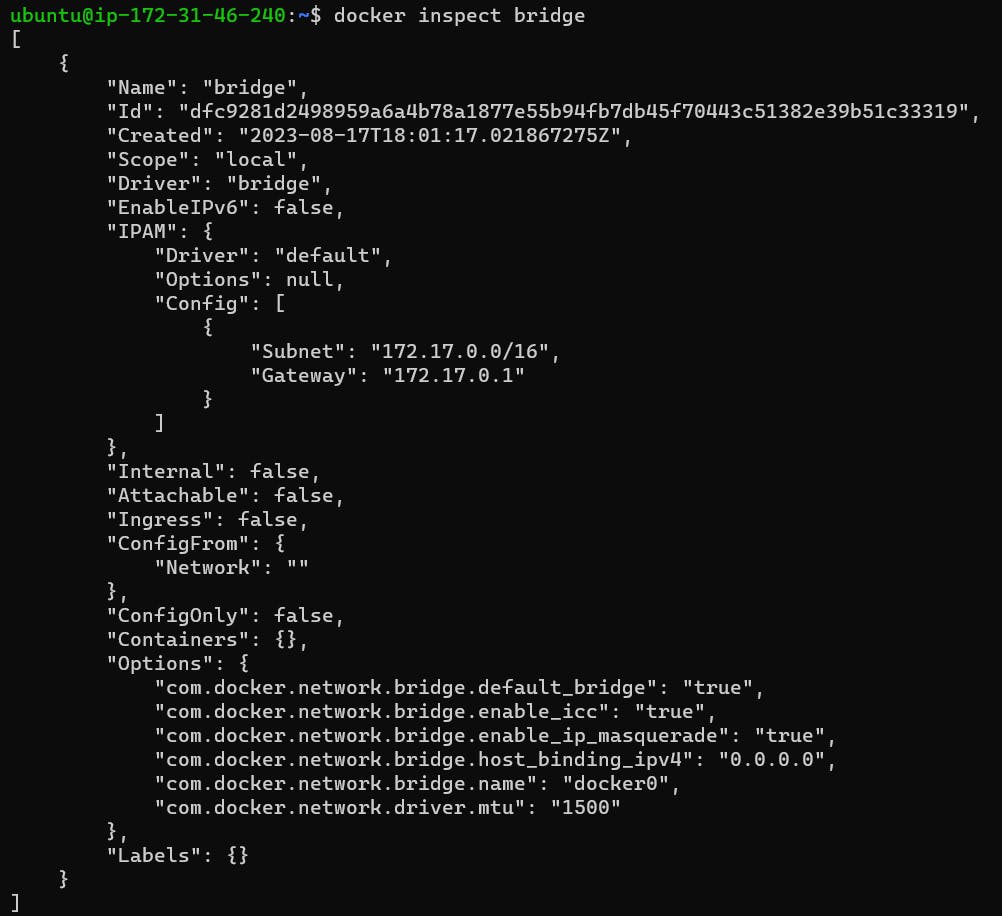
So, if you are on your terminal and you write docker inspect bridge, you get this whole detailed info about the default bridge. You can see the bridge has its Id and IP.
Host network
When a container runs on the host network, it bypasses the docker default network and uses the host system's network. This mode does not create a separate network stack for a container. The container shares the same network stack with the host which means the container also has full access to the network interfaces of the host.
In the below picture you can see a few things written, let me explain to you what are these. So when you do not have docker installed on your system you just have the lo and eth0 , lo is a local network within the system and eth0 is the host network for connections outside the system. When docker is installed docker0 also comes in the network space also known as the default bridge. Here you can understand that if you work on the host network your network shifts on eth0 and if you work on the default bridge your network works on docker0.
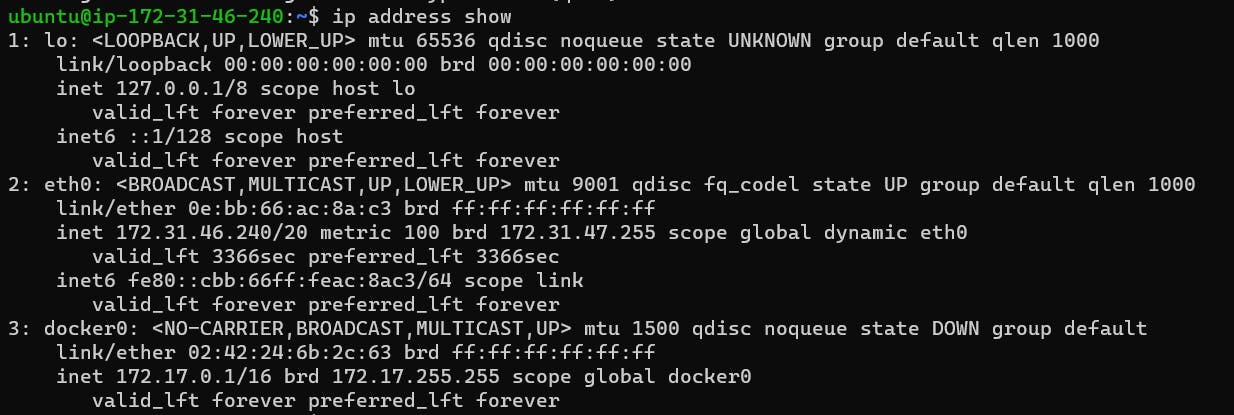
Before discussing the default network let's do some hands to understand how the Default bridge works.
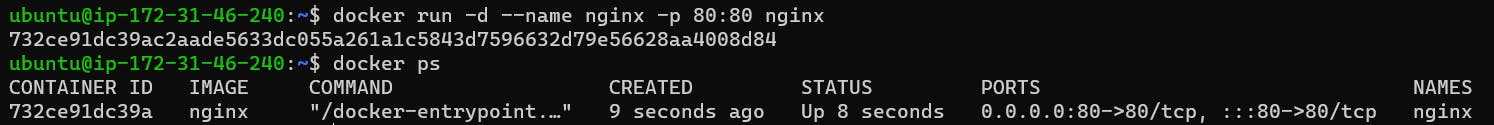
So here I run an Nginx image on port 80. This is running on the default bridge network. When on the browser we type IP of instance/80, the Nginx web page opens.
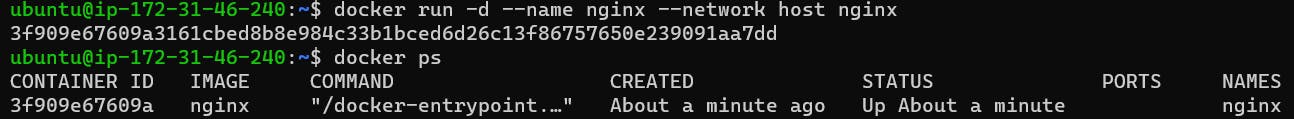
In the above image, you can see this time I am running my container on the host network. So this time there is no need to specify the port number you can directly run it via the instance IP.
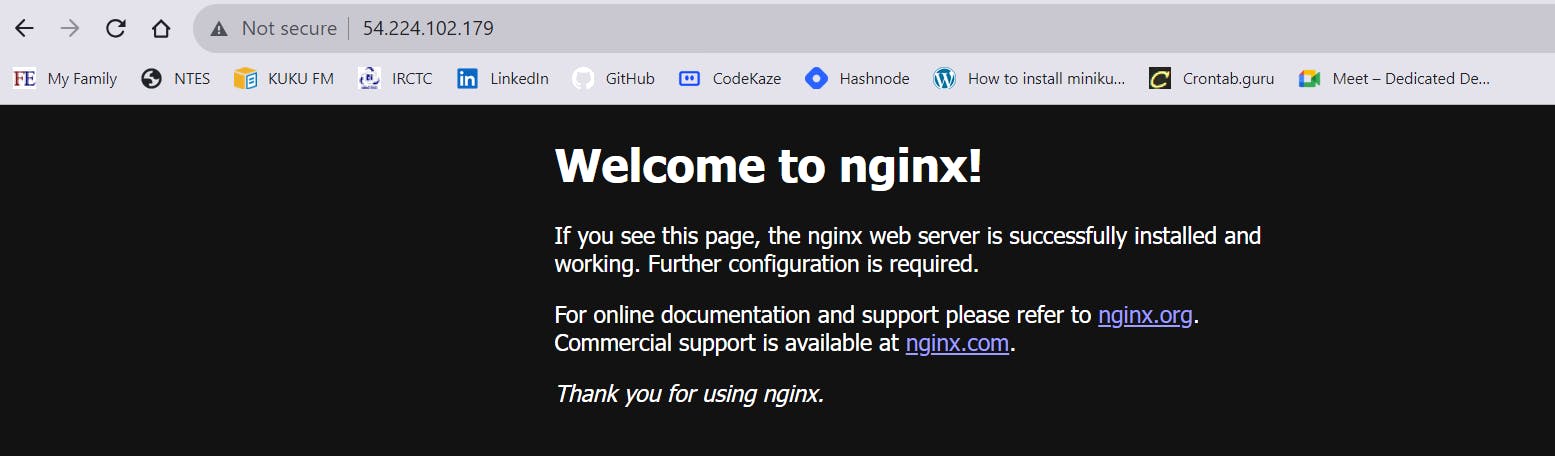

In the above image, you can see the host does not have a Mac, ipv4 and ipv6 address of its own because it uses the host's IP address.
Custom Bridge Network
#command to create a custom network.
docker network create tws-bridge
Now I am running my Nginx container in my custom container.
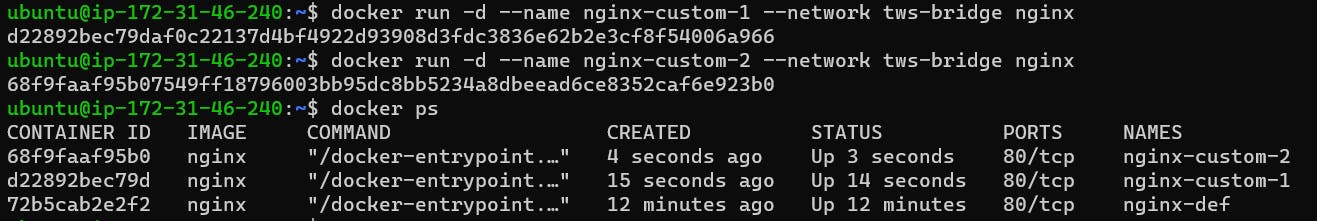
So if you set up more than one container on the same custom network you can now access that container easily and containers can communicate with each other and containers not in that network will not be able to access it.
Let's demonstrate it with an example. The container that you have created, execute it-
docker exec -it <containerID> sh
# inside the container terminal write:
ping <other container id in the same network>
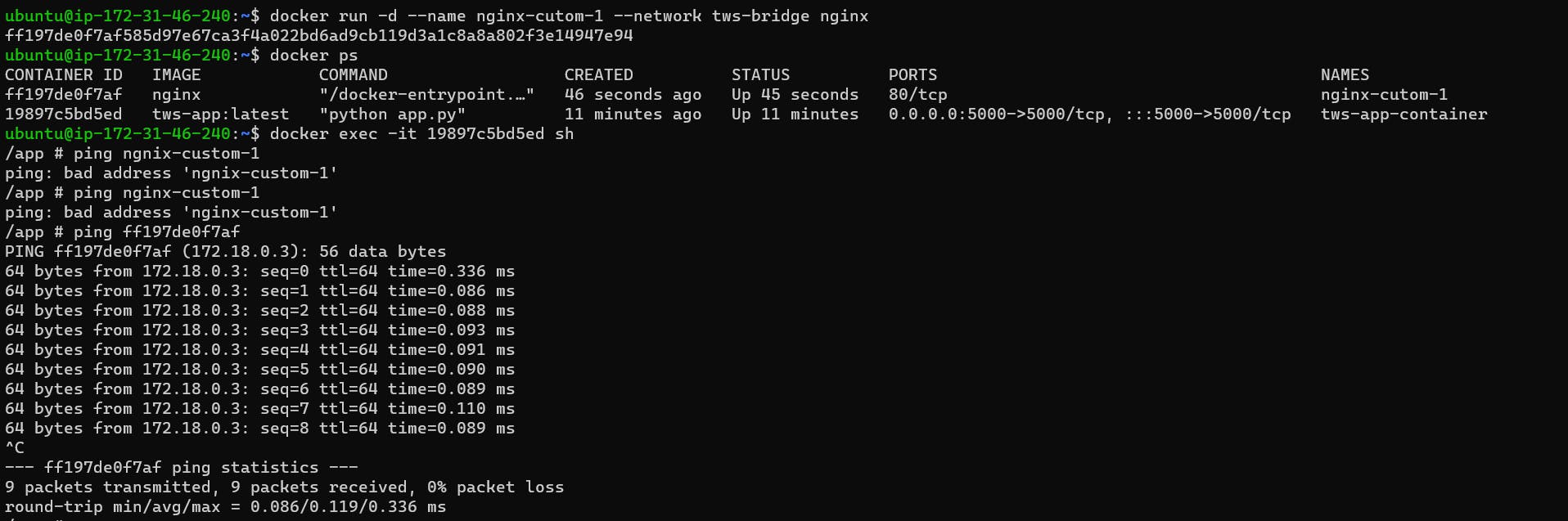
In the above picture, you can see that container easily connects with another container.
So, we have learnt about custom networks let's go by creating a Project.
# repo link
https://github.com/CoolSrj06/microservices-k8s.git
So, I first built the Docker image from the docker file and ran the image on my custom network on port 5000.
# Here the code
docker run -d --name python-app --network tws-bridge -p 5000:5000 python-app
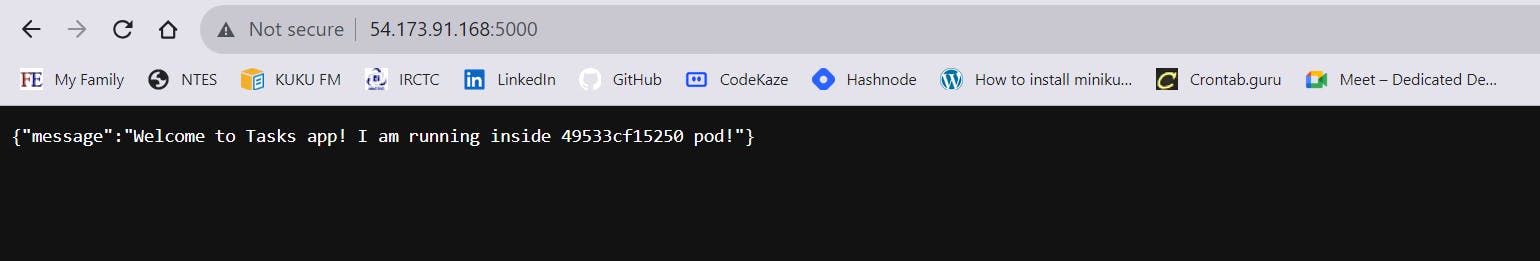
Congrats, you have hosted your application on the instance through your private network.
Now, if you go inside the k8s file in your repo you will find the app.py file there it's coded that if your browse /task our app will connect to mongo.
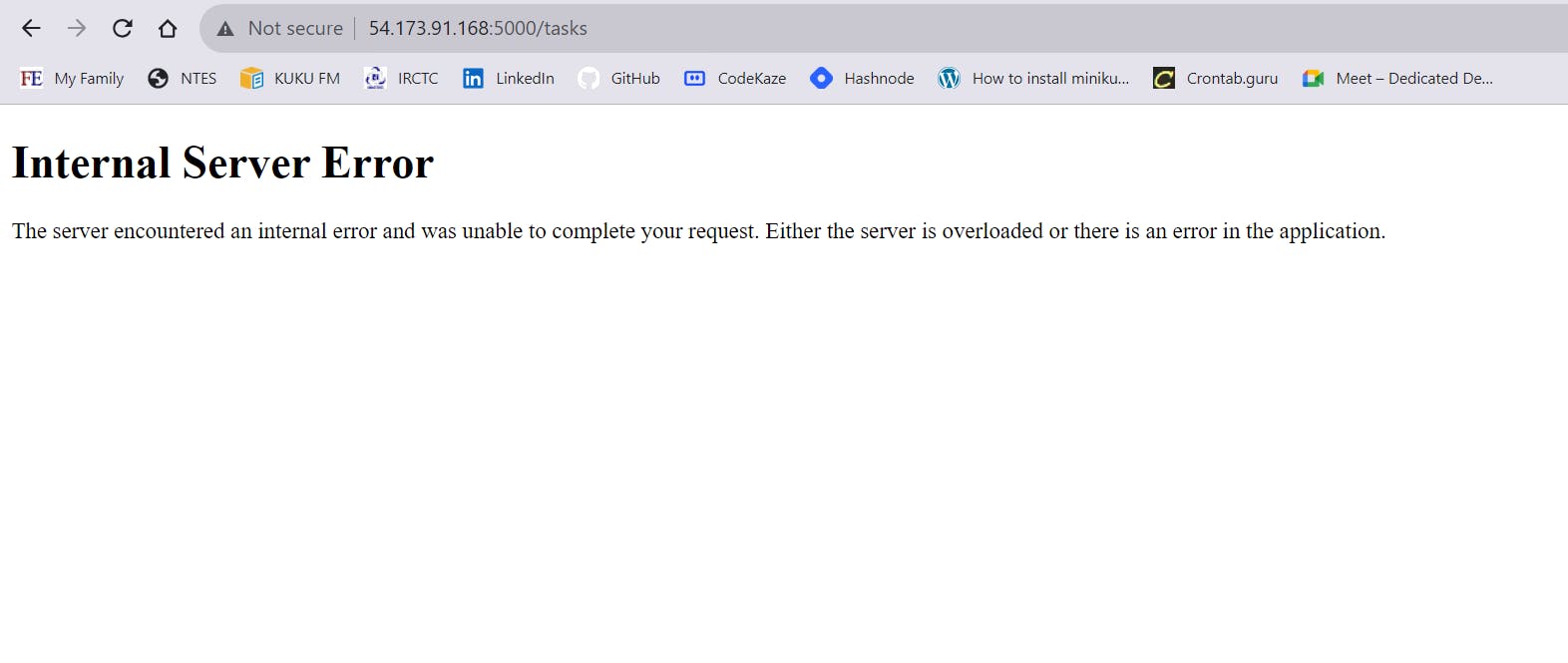
So if you try to do that you will see that it says Internal server error. This is because your Mongo container is not present on your network.
Below is the small part of the log of your app container where it is trying to connect to Mongo but is failing.
docker logs <container id>
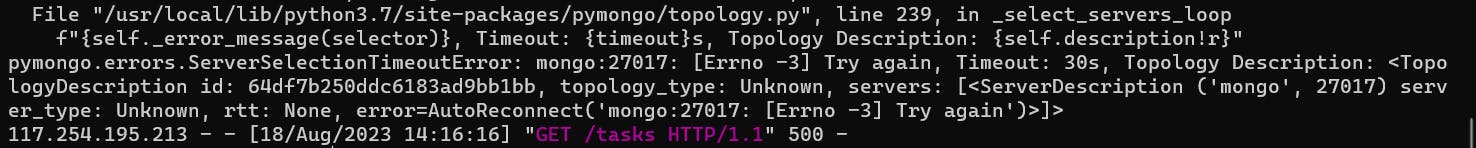
Now let's create and add a Mongo container on our tws-bridge network.
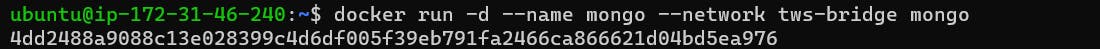
So we have done this task. Now if we try to run the same url lets see what happens.
Hurray!! we have successfully created a project where we created a default network for two Teir applications using docker.
After having done this let's learn and finish the other types of docker networks:
Overlay Networking
Overlay networks span across multiple Docker hosts, creating a unified communication layer for containers across a cluster. This is essential for scenarios where containers need to communicate seamlessly across different hosts. Technologies like VXLAN facilitate this by encapsulating traffic and routing it appropriately.
None Networking
In Docker, the "none" network mode is a networking option that effectively disables networking for a container. When a container is run in the "none" network mode, it does not have access to any networking resources, which means it cannot communicate with the network or other containers.
Containers running in the "none" network mode are completely isolated from the network, and they do not have access to the loopback interface or any external network interfaces. This can be useful in scenarios where you want to run a container that doesn't require any network connectivity, such as running a one-off script or debugging a container without involving networking.
MAC VLAN
A MAC VLAN (short for MAC Virtual LAN) is a type of network virtualization technology used in Linux-based systems, including Docker, to create multiple network interfaces with different MAC addresses on a single physical network interface card (NIC). MAC VLANs allow you to assign separate MAC addresses to different containers or virtual machines running on the same physical host, effectively providing isolation at the MAC address level.
IP VLAN
An IP VLAN (short for IP Virtual LAN) is a networking concept that involves segmenting a physical network into virtual sub-networks based on IP addresses. IP VLANs provide a way to isolate different groups of devices or systems on a network while using the same physical network infrastructure. This segmentation is achieved by assigning different IP subnets to different VLANs.
Here my blog on Docker networking ends. Grateful for your time.
Your suggestion and criticism are welcomed.